Excluding file types from a scan
Invicti ignores some URLs that do not need to be tested, using a list of excluded file types or extensions.
By default, Invicti ignores common file types such as image files (.jpg, .png, etc.) and video files (.mp4, .avi, etc.) as they are not typically a source of web application vulnerabilities. You can modify this list of excluded file types from the Extensions tab when configuring a Scan Policy.
Excluding Binary Files
Invicti can also detect binary files but, by default, does not test them. These files are outside the scope of scanning a web application for vulnerabilities. In fact, the Invicti scanners have a built-in mechanism to check if HTTP responses are binary responses; if they are, they will be excluded from tests.
If you have several binary files on your website, add their extension to this Extensions list, so that when Invicti identify them, it does not have to make the binary check. The advantage is that this shortens the scan duration.
Crawl and Attack Options
This table lists and describes the crawl options in Invicti.
|
Crawl Option |
Description |
| Do not Crawl | Invicti does not crawl file links and adds them to the Out of Scope with Extension Blacklisted reason. |
| Crawl | File links will be crawled. |
| Crawl Only Parameter | File links will be crawled if they have any Query String parameters. Otherwise they will be added to the Out of Scope with Extension Blacklisted reason. |
This table lists and explains the attack options in Invicti.
|
Attack Option |
Description |
| Do not Attack | File links will be ignored. |
| Attack Parameters | File links will be analyzed if they have a parameter.
For example:
|
| Attack Parameters and Query String | File links will be analyzed if they have a parameter or Query String.
For example:
|
How to Exclude File Types From a Scan in Invicti Enterprise
- From the main menu, click Policies, then Scan Policies.
- Do one of the following (see Overview of Scan Policies):
- Next to an existing policy, click Clone
- From the main menu, click Policies, then New Scan Policy
- In New Scan Policy window, click the Extensions tab.
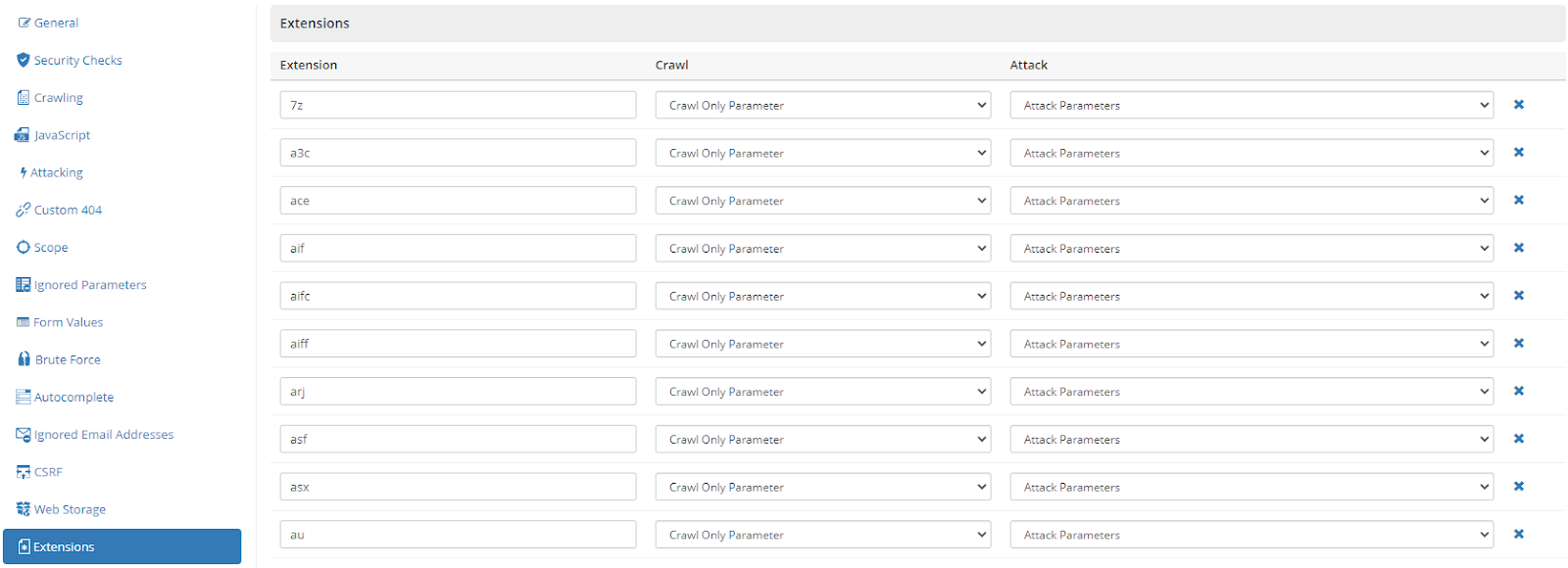
- You can create a new exclusion or edit an existing one. Either:
- Select an existing item by clicking into its EXTENSION field.
- Click New to create a new, blank Extensions row.
- Enter the extension you want to exclude in the EXTENSION field
- From the CRAWL dropdown, select an option (see Crawl and Attack Options).
- From the ATTACK dropdown, select an option (see Crawl and Attack Options).
- Click Save.
How to Exclude File Types From a Scan in Invicti Standard
- From the Home ribbon, click New. The Start a New Website or Web Service Scan dialog is displayed.
- From the Scan Policy section, click the ellipsis (
 ) to open the Scan Policy Editor.
) to open the Scan Policy Editor. - Do one the following (see Scan Policy Editor):
- From the list at the top of the dialog, select an existing Scan Policy (avoid the default ones as they can’t be customised)
- Alternatively, select an existing Scan Policy and click Clone
- Click New
- From the left-hand menu, click Extensions.
- You can create a new exclusion or edit an existing one. Either:
- Click into the last (blank) row in the Extensions table
- In the Extension field, enter the extension you want to exclude
- Select an existing item by clicking into the Extension field
- Click into the last (blank) row in the Extensions table
- In the Crawl column, click into the cell and from the dropdown, select an option (see Crawl and Attack Options).
- In the Attack column, click into the cell and from the dropdown, select an option (see Crawl and Attack Options).
- Click OK.