Automating Penetration Testing of Websites
Use the Invicti security scanner as your penetration testing software to automatically identify vulnerabilities and security flaws in your web applications, web services and web APIs.
Determined malicious hackers want to find and exploit security vulnerabilities in web applications. They have access to the same penetration testing software and security tools that security professionals use to conduct security assessments.
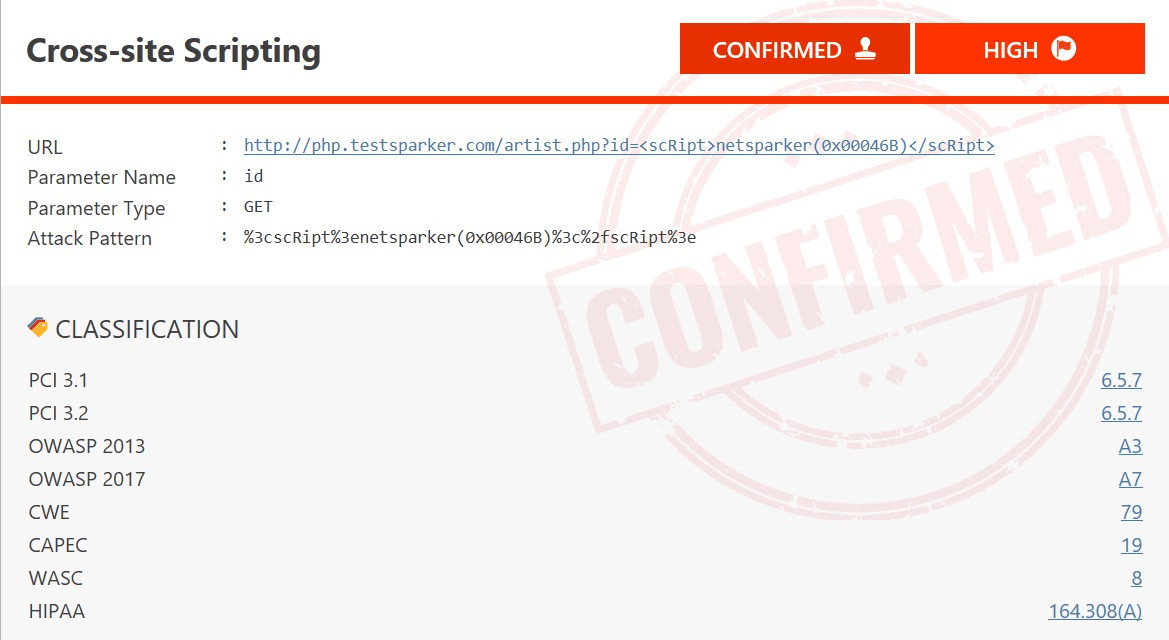
To stay conversant with the always evolving cyber security threats, businesses have to emulate their attackers with the Invicti web application security scanner. Invicti enables you to do penetration tests on web applications to discover attack surfaces and perform security testing. During the automated web application penetration tests the Invicti scanner checks the targets for thousands of vulnerability variants such as SQL injection and cross-site scripting (XSS).
Continuous Web Application Penetration Tests
Manual penetration testing is expensive and time consuming. Also, it slows down the development cycle and only provides businesses with a mere snapshot overview of the security state of their web applications.
On the other hand an automated vulnerability assessment tool such as Invicti allows businesses and pen testers to do thorough software and application testing. Businesses can conduct automated and continuous penetration tests on their web applications minus the expensive budgets and an army of skilled penetration testers. Penetration testing software such as the Invicti web vulnerability scanner empowers businesses to scan thousands of web applications and web APIs for security vulnerabilities within hours. They also can repeatedly scan web applications within the SDLC, thus avoiding suffering any security breaches in live environments.
Scan Every Web Application and Web API
Coverage, i.e. the ability to crawl a website, is very important in penetration testing tools. If the vulnerable parameter is not crawled then the vulnerabilities in a web application cannot be identified. It is this coverage that sets the Invicti web application security scanner apart from the other penetration testing tools.
Independent comparisons have shown that Invicti is the web application penetration testing software that has the best coverage and scans for the broadest range of vulnerability types.
Invicti uses a Chrome based crawling engine that can understand and crawl any type of legacy and modern web application. Invicti’s crawling engine fully supports JavaScript, and it can crawl HTML5, Web 2.0 applications, Java, Single Page Applications and any other application that relies on JavaScript frameworks such as AngularJS and React. Invicti can crawl and scan any web application that is available on the HTTP and HTTPS protocols.
Speed and Efficiency Through Accuracy
The biggest pain point of automated testing tools, especially free pen testing software are false positives. Like false alarms, false positives are the source of many problems. Because of false positives users don’t trust the pen testing tool, and, instead, resort to spending weeks manually verifying the identified web application vulnerabilities.
Atypical in relation to all other penetration testing tools, Invicti uses its pioneering Proof-Based Scanning™ technology. It automatically verifies identified vulnerabilities, demonstrating that they are not false positives. With Proof-Based Scanning™, penetration testers and security professionals do not have to manually verify the findings. This agility allows them to truly scale up their efforts and scan thousands of web applications effortlessly in hours.
Ease Triaging of Vulnerabilities with Integration
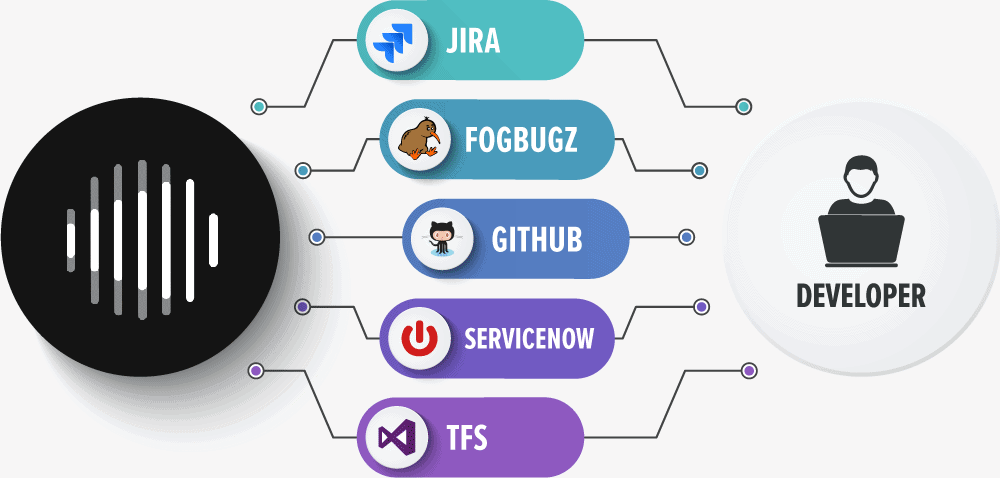
Invicti surpasses the capabilities of traditional web application security software and black box scanners. It has built-in workflow and vulnerability management tools. In addition, it provides out-of-the-box support for issue tracking systems and continuous integration and deployment servers, including:
- Atlassian JIRA
- Github
- Atlassian Bamboo
- JetBrains TeamCity
- Microsoft Team Foundation Server (TFS)
It also has a fully fledged REST API which eases the integration with your SDLC, DevOps and other development environments, regardless if they are built on Linux or Windows operating systems.
Stay on Top of the Web Security Game with the Right Reports
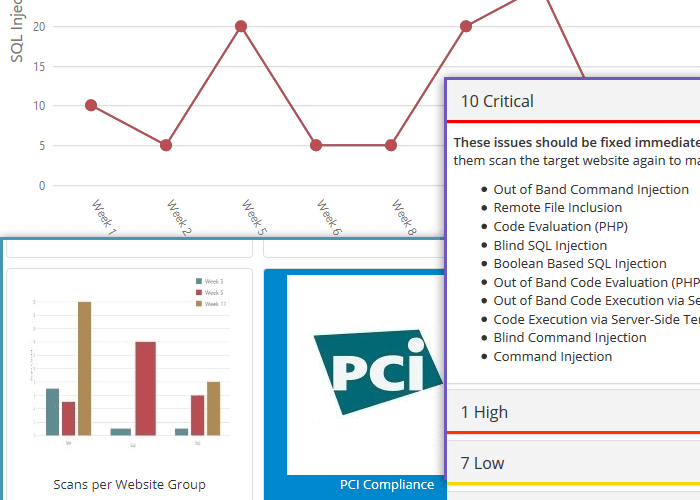
Keeping thousands of web application secure is a team effort. It is about collaboration and impeccable orchestration of resources, which cannot be achieved without the right reports. Invicti’s web application security solution has reports for managers to review developers’ progress. The Invicti reports allow managers to gain an overview of the security state of all web applications, web APIs and services.
It also has detailed reports for penetration testers and developers. Technical reports include all the technical details developers need to understand the reported security vulnerabilities. In the technical reports Invicti also recommends practical remedial actions developers can follow to address the security issues. In case of compliance, it is also possible to generate reports to meet the regulatory compliance requirements such as those in PCI DSS and OWASP Top 10.
Apply for a free trial today of the Invicti web application security solution and upgrade your pen testing! Invicti is available as an on-premises, hosted and self-hosted solution.
What our customers are saying
“I had the opportunity to compare external expertise reports with Invicti ones. Invicti was better, finding more breaches. It’s a very good product for me.”

Bruno UrbanOECD
“As opposed to other web application scanners, Invicti is very easy to use. An out of the box installation can detect more vulnerabilities than any other scanner.”

Perry MertensING Bank
“We chose Invicti because it is more tailored to web application security and has features that allow the university to augment its web application security needs.”

Dan FryerOakland University