Sound Hijacking – Abusing Missing XFO
This article examines a new attack on Google Docs called Sound Hijacking, which leads to the takeover of users’ audio input devices. We investigate how the attack works and conclude with an evaluation of the importance of the X-Frame-Options Header for the attack and information on which browsers support it.
Your Information will be kept private.
Stay up to date on web security trends
Your Information will be kept private.

A Clickjacking attack works by loading a malicious website inside a low-opacity iframe and overlaying it with an innocuous looking button, checkbox or link. This tricks the user into interacting with the vulnerable website beneath. The user is then forced to click the apparently safe UI element, triggering a set of actions on the embedded vulnerable website.

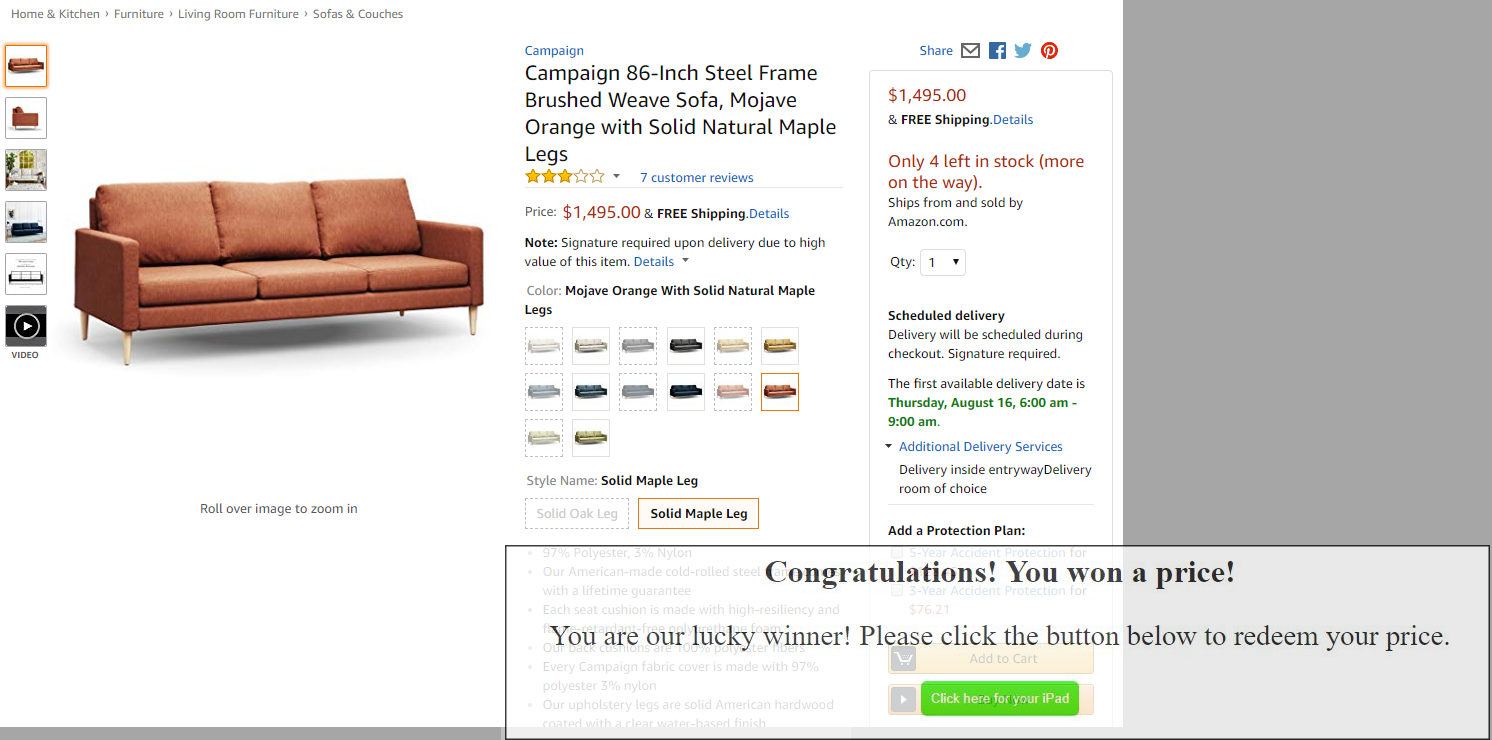
The Methodology of the Sound Hijacking Attack
Google enabled Chrome users to use their voice to 'write' into documents and sheets (Tools>Voice Typing).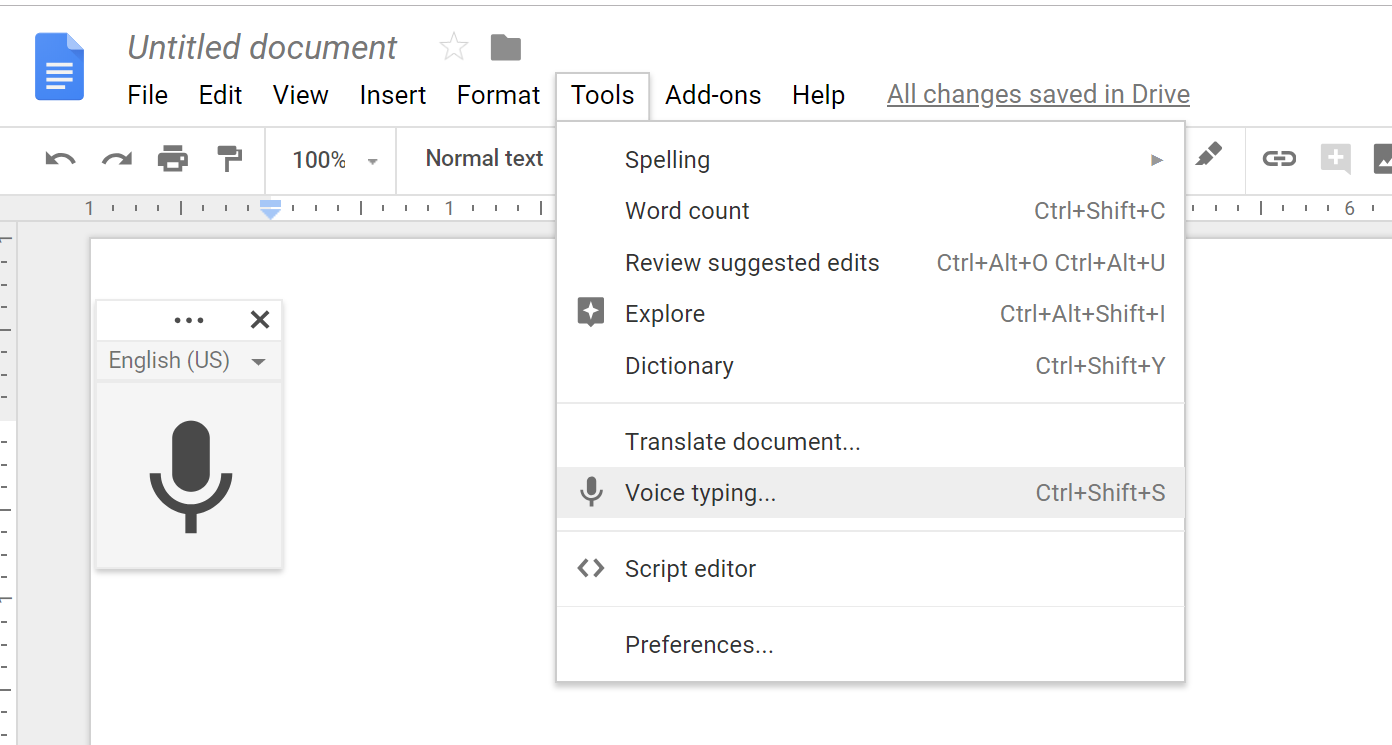
<iframe src=“https://docs.google.com/document/d/XXXXXXX/edit” allow=“microphone *”></iframe>Feature Policy Mechanism
It's important to note that the allow attribute on the iframe command plays a crucial role in this scenario. This Feature Policy mechanism enables developers to control the browser features that receive user data, using commands specific to each website:- Location information
- Microphone and camera use
- Multimedia controls
- Gyroscope sensors etc
- And, more
The Importance of X-Frame-Options Header in Preventing Clickjacking Attacks
As illustrated, the lack of X-Frame-Options (XFO) header is used to exploit unique attack vectors.
- It should be present in the HTTP response of every page
- The frame-ancestors directive of the Content Security Policy (CSP) header can be used instead of X-Frame-Options
Content-Security-Policy: frame-ancestors 'none'; // Doesn’t load any URLs within an iframe.Content-Security-Policy: frame-ancestors 'self'; // Has the same use as the SAMEORIGIN parameter.Which Browsers Support the X-Frame-Options HTTP Header?
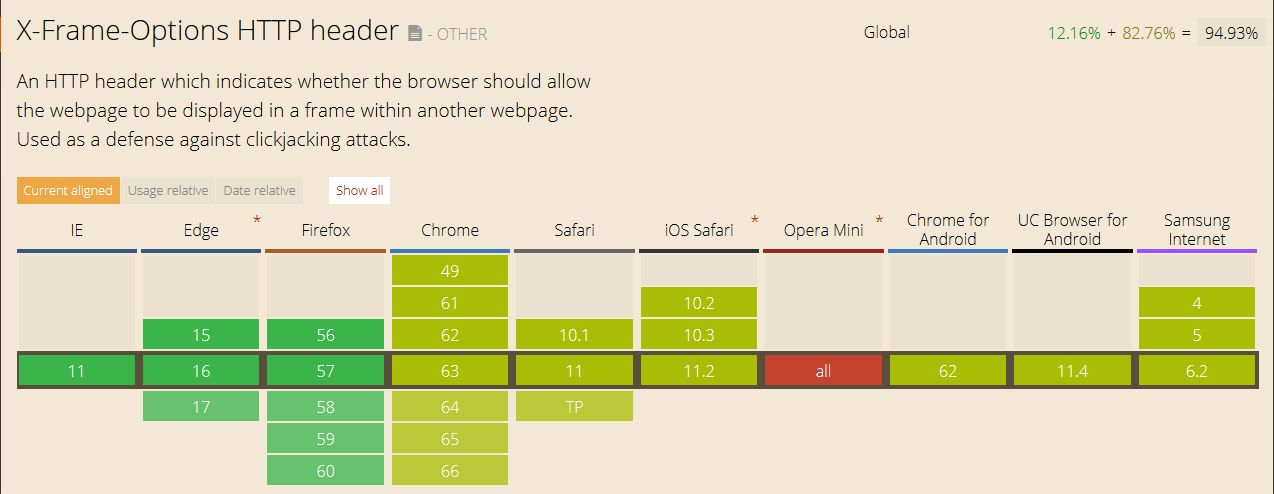
Like many security features, the X-Frame-Options header was not always available in browsers. Instead, the need for such a header became apparent much later. Not all browsers supported it in their first versions. Thankfully, however, almost all modern browsers support X-Frame-Options, either fully or partially.