June 2019 Update for Netsparker Enterprise
This blog post announces updates for June’s 2019 release of Netsparker Enterprise. Highlights include auto update support for scanner agents, API endpoints for managing issues, and a new Managing Issues (Restricted) permission. There are also new scan policies for PCI and OWASP, a Best Practice severity level, and support for OAuth2 and RESTful API.
Your Information will be kept private.
Your Information will be kept private.
We're delighted to announce a Netsparker Enterprise update. The highlights in this update are auto update support for scanner agents, an improved Manage Agents page, a new API endpoints for managing issues, and a new Manage Issues (Restricted) permission.
Other updated features in June 2019 for Netsparker Enterprise are new scan policies for PCI and OWASP Top Ten vulnerabilities, a new Best Practice severity level for vulnerabilities that are recommended practices but not critical, and added support for OAuth2 Authentication and the RESTful API Modeling Language (RAML) link import.
This announcement highlights what is new and improved in this latest Netsparker Enterprise update.
Auto Update Support for Scanner Agents
Netsparker Enterprise allows users to install and configure scan agents to conduct scans and then report the results back to Netsparker Enterprise. Agents are used when the target website is only available from your local network and not accessible from the internet, or when your are using the Netsparker Enterprise On-Premises edition.
With this latest update, users can now enable automatic updates for each Agent instead of manually upgrading using installation files on the local machines. Enabling Auto Update means that when a new version of the Netsparker Enterprise Scanning Agent is available, the target agent will update itself as soon as possible.
As this is implemented in the latest release, current users have to manually upgrade to the latest version once final time. After that, they can use Auto Update feature as required. If the user wants to make updates fully automatic, they click Enable Auto Update. No other action is required. Users can disable this new feature by clicking Disable Auto Update in the same menu.

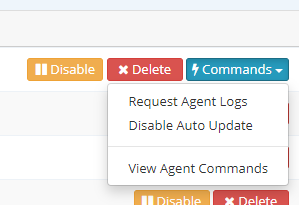
For further information, see Installing Internal Agents.
Accessing Agent Logs
The Netsparker Enterprise Scanning Agent stores application logs under the Logs folder in the installation path. You can now both request and download agent logs. These logs are requested and confirmed from the Manage Agent page. With the latest version of the Agent, the last three days’ logs can then be downloaded from the same place. These logs are useful for troubleshooting.

For further information, see Internal Agents in Netsparker Enterprise (On-Demand) and Agents in Netsparker Enterprise On-Premises.
New API Endpoints for Managing Issues
In Netsparker Enterprise, you can view lists of Issues with all their details, each representing either a vulnerability or other useful information detected during a web application security scan.
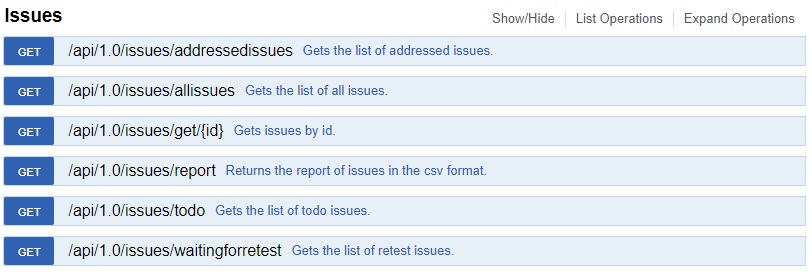
This latest update, a popular customer request, brings this capability to the Issues API Endpoints, enabling you to easily integrate with other applications or internal systems. You can now use the API Endpoints to view the following:
- Addressed Issues list
- All Issues list
- Issues by Id list
- Report of Issues in CSV format
- To Do list
- Waiting for Retest list
For further information, see What Systems Does Netsparker Integrate With?.
New Manage Issues (Restricted) Permission
We have added a new Manage Issues (Restricted) permission to the Permissions Matrix to help Account Owners manage what new Team Members can do in Netsparker. This new permission level enables you to restrict what users can do with detected Issues.
Users assigned this permission level are unable to update the State of an issue to Accepted Risk or False Positive.
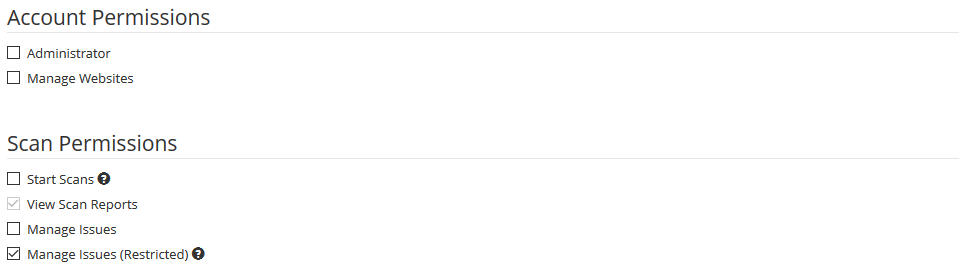
Instead, they can only mark issues as Fixed (Unconfirmed), and view scan reports.
For further information, see Viewing Issues in Netsparker Enterprise.
Scan Policies for PCI and OWASP TOP 10 Vulnerabilities
The Open Web Application Security Project (OWASP) is a worldwide, non-profit organization that publishes a top ten list of critical software risks to encourage security and best practice in the web community. The Payment Card Industry (PCI) Security Standards Council sets requirements for security compliance that are the benchmark for the entire industry.
We have added default scan policies for OWASP Top 10 vulnerabilities and PCI vulnerabilities. You can now run web application security scans using these Scan Policies to detect OWASP Top Ten vulnerabilities and receive approved PCI compliance reports for their websites.

For further information, see Using Netsparker To Comply With The OWASP Application Security Verification Standard When Developing Web Applications and PCI Scanning Announcement.
New Best Practice Severity Level
The new Best Practice severity level is for issues that are recommended practices but are not critical. They aren’t vulnerabilities and are less serious than Information Alerts. But they represent practices that are regarded within the web application security industry as superior to alternatives because they produce secure results and have become the standard way of doing things for software industry leaders.
For further information, see Vulnerability Severity Levels.
New OAuth2 and RESTful API Support Features
The Netsparker Enterprise update of June 2019 has added support for both OAuth2 authentication and RESTful API. This new feature will allow users to configure scans for websites that require OAuth2 authentication and automate the login process.
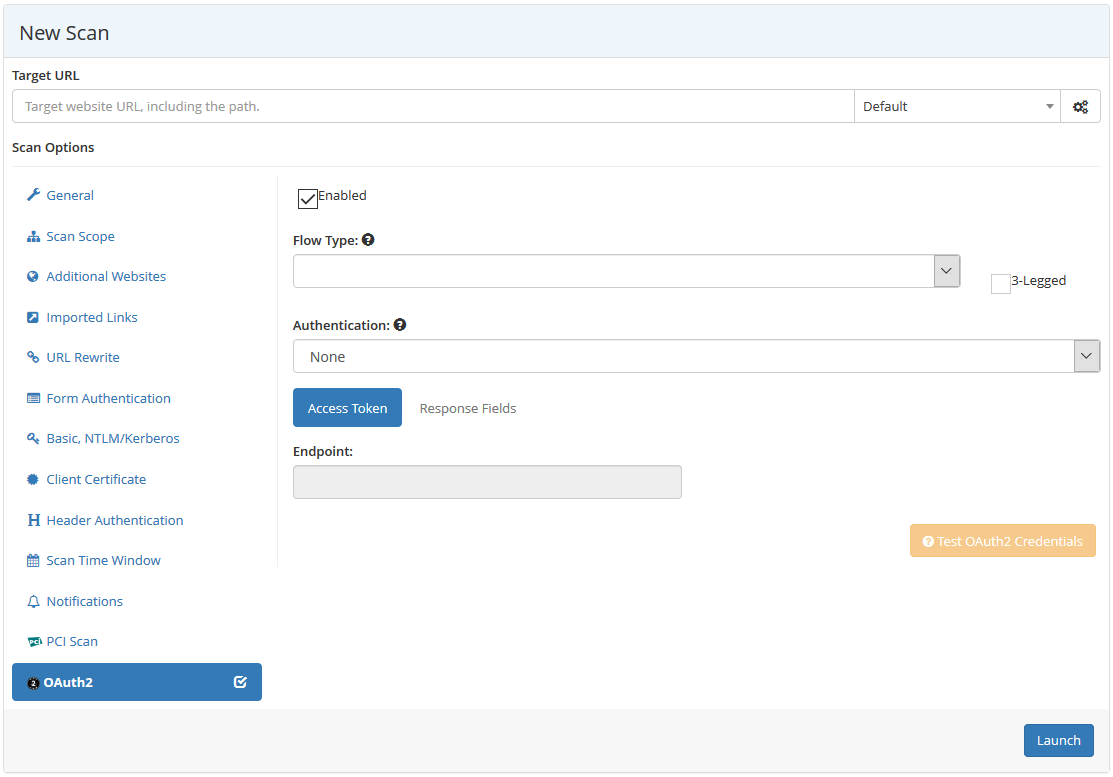
Users also have support for RESTful API modeling language (RAML) link imports and links from WordPress REST API files.
For further information, see Finding Vulnerabilities in RESTful Web Services Automatically with a Web Security Scanner.
Further Information
For a complete list of what is new, improved and fixed in this update, refer to the Netsparker Enterprise.






