January 2017 Netsparker Enterprise Update
This post gives an overview of the new features introduced in the January 2017 update of Netsparker Enterprise. It also lists down all the new web application vulnerability checks Netsparker Enterprise has.
Your Information will be kept private.
Your Information will be kept private.
During the end of 2016 and start of 2017 festive season, our developers were planning and developing the next Netsparker Enterprise update. For a change they came up with something innovative, something that no other vendor has done yet; form authentication and session verification in an online web application security scanner.
And that’s not all! Read this post for an overview of what is new and improved in the first Netsparker Enterprise update for 2017!
Authentication & Session Verification for Form Based Authentication
Prior to this release it was not possible to verify the credentials you have configured in Netsparker Enterprise when scanning a password protected website. This meant that you can only find out if the configuration is correct once the scan is finished. This means that if the credentials were not correct, the scan would have been a waste of time and resources.
To solve this issue our developers built a new login verification system, so now you can verify the configured credentials before launching a scan. Also, should you wish you can also modify the logout detection pattern when configuring form authentication.
Read the article Configure Authentication and Verify the Credentials in Netsparker Enterprise for more detailed information on how the new form authentication verification system works.
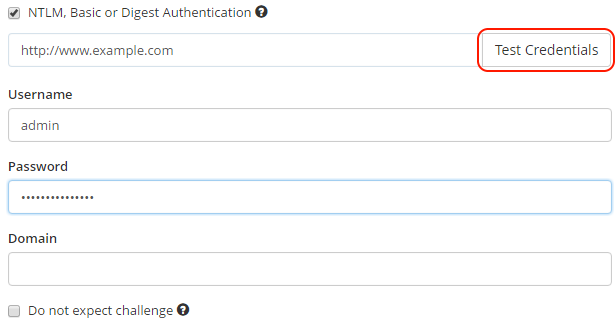
Verification of Credentials for Basic and NTLM/Kerberos Authentication
We also added authentication verification to Basic and NTLM/Kerberos authentication. Therefore when scanning a website with such authentication mechanism, do not forget to click the button Test Credentials prior to launching a web vulnerability scan.
Support for Netsparker Hawk
Netsparker Hawk is a vulnerability testing infrastructure we announced earlier on this year. It is used by Netsparker Enterprise and Netsparker Desktop to automatically detect vulnerabilities that cannot be detected using the typical request-response method. With the aid of Netsparker Hawk the scanner can now identify the following vulnerabilities:
- Out-of-band Code Evaluation
- Out-of-band Command Injection
- Out-of-band Remote File Inclusion (RFI)
- Out-of-band SQL injection
- Blind cross-site scripting (XSS)
- XML External Entity (XXE) Injection
- Server-side request forgery (SSRF)
Read How the Netsparker web vulnerability scanner finds SSRF and out-of-band vulnerabilities for more detailed information on the Netsparker Hawk vulnerability testing infrastructure.
Other Netsparker Enterprise Updates for January 2017
Apart from the above highlights we also added automatic confirmation of the Frame Injection vulnerabilities, improved the performance of the DOM simulations, updated the off-the-shelf web applications vulnerability database, improved the coverage of open redirects and much more. Please refer to the Netsparker Enterprise changelog for a complete list of what is new, improved and fixed in this update.





