
Prospects frequently ask us how do
Netsparker web application security scanners compare to other competitor scanners. This type of due diligence is part of any procurement or investment in new, or additional technology. I wouldn't fork out a few thousands without doing my homework.
There are many factors you should look into when comparing automated web security tools as explained in
How to evaluate web application security scanners, but I won't go into all of that. In this post I will look specifically into the scanning engine's capability, which is the most important component of the scanner. If that does not work properly, then all the other frills are worthless.
2013 and 2014 Web Security Scanners Comparison
Looking back at the
independent web application security scanner comparison done by Shay Chen (
@sectooladdict) in 2013 and 2014, Netsparker outperformed all competitors, except one, to take overall second place. We would have taken first place, and equaled the performance of a scanner that costs at least three times as much if it wasn't for a weird bug which we fixed within a few minutes. Tough luck? Not much. Motivated? Yes. Such results motivates us to work even harder and continue improving both the desktop and the
online web application security scanner and keeps us striving to be number one.
How Does Netsparker Scanners Compare with Other Scanners in 2015?
A few weeks back Shay Chen updated the results using the latest version of the Netsparker scanning engine, which is used in both Netsparker Enterprise and
Netsparker Desktop web security scanner. Below are the results:
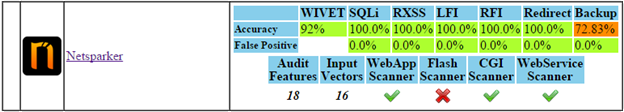
Direct Impact Vulnerabilities
Netsparker detected all the
SQL Injections, reflected
Cross-site Scripting, Local File Inclusions and Remote File Inclusions vulnerabilities without reporting any false positives. These vulnerabilities are all direct impact vulnerabilities and are the most commonly exploited ones during an attack.
Old Backup Files Detection - Non Direct Impact Vulnerability
We also improved the backup files detection rate of the Netsparker scanners. Last year Acunetix led this security check with 32.61% and this year we identified 72.83%. Pretty good job there!
Why Netsparker Focuses More on Direct Impact Vulnerabilities?
After the web application security scanners comparison of 2014, we continued working on improving the scanning engine. These improvements always focus more on direct impact vulnerabilities such as Cross-site scripting, SQL Injection,
DOM XSS etc.
The reason behind such decision is very simple; if malicious hackers identify a direct impact vulnerability on your web application they can exploit it within minutes, which leads to a hacked website, loss of records, tampering of data etc. For example by exploiting a SQL injection vulnerability malicious attackers can gain unauthorized access to the web application's database which typically contains sensitive information about your business and customers. They can also tamper or delete such data. In case of a cross-site scripting vulnerability, the attackers can hijack your users' session, where typically the administrator is targeted.
On the other hand, even though old backup files can contain juicy information for attackers, most of the time they do not contain enough information to craft an attack. Also, such type of files can be easily identified during a quick manual analysis. For example if you do a recursive file and directory listing of your web application you can easily spot such files within a minute or so.
We are not saying these type of possible security flaws are of less importance and less of a focus for Netsparker. On the contrary, we in fact outperformed any other scanner in 2014 when measured against this performance metric and
Netsparker detects a wide range of web application vulnerabilities. However, our main focus will always be to help users identify all sort of direct impact web application vulnerabilities, those which are very difficult to find manually, or those that are time consuming.
How Useful Are Web Security Scanner Comparisons?
At Netsparker we always say that the best way to test a web application security scanner is to scan a staging copy of your web applications as explained in
How to evaluate web application security scanners. It is important to scan a staging copy of your own web applications because each web application has individual characteristics, therefore each scanner can report different results. Every developer has his own way of writing code and every administrator has his own way of configuring servers and web applications, so nothing beats a scan of your own web applications.
Though because it is virtually impossible to test all scanners available in the market today, these comparisons are incredibly useful and highlight who are the market leaders, the scanners that can detect the most vulnerabilities. And when looking for a scanner that is what you are looking for, automating the process of identifying all possible web application vulnerabilities. Therefore if you would like to test web application security scanners, or as they are also called web vulnerability scanners choose the top three from such lists and get your hands dirty.
 Prospects frequently ask us how do Netsparker web application security scanners compare to other competitor scanners. This type of due diligence is part of any procurement or investment in new, or additional technology. I wouldn't fork out a few thousands without doing my homework.
There are many factors you should look into when comparing automated web security tools as explained in How to evaluate web application security scanners, but I won't go into all of that. In this post I will look specifically into the scanning engine's capability, which is the most important component of the scanner. If that does not work properly, then all the other frills are worthless.
Prospects frequently ask us how do Netsparker web application security scanners compare to other competitor scanners. This type of due diligence is part of any procurement or investment in new, or additional technology. I wouldn't fork out a few thousands without doing my homework.
There are many factors you should look into when comparing automated web security tools as explained in How to evaluate web application security scanners, but I won't go into all of that. In this post I will look specifically into the scanning engine's capability, which is the most important component of the scanner. If that does not work properly, then all the other frills are worthless.








