Proxy
A proxy is a program or device that is used as an intermediary, to intercept all the traffic between clients and the internet. Proxies can be used as a content filtering mechanism in corporate environments, to protect privacy for example. They can also be used for debugging purposes.
The use of a proxy may be helpful during a scan if the rules require that all requests should originate from a specific source IP or range of IPs. Since Invicti is used in such environments, it is necessary it’s also configured in Invicti.
In Invicti Standard, you can select to use the system or custom proxies, or to use none. Invicti will use the selected proxy for connecting to target websites and receiving updates. You can also configure the proxy settings that will be used in the Scan Policy scope.
Proxy Options
This table lists the Proxy options.
| Option | Description |
| Use System (Internet Explorer) Proxy | Select to use the System Proxy. This is the default. System Proxy is the system-wide proxy that is used by every program by default. |
| Use Custom Proxy | Select to use and configure a Custom Proxy. Custom Proxy should be configured explicitly to be used, unlike System Proxy. |
| Do Not Use Proxy | No Proxy will be used. |
How to Configure Proxy Options in Invicti Standard
- Open Invicti Standard.
- In the Home tab, click Options. The Options dialog is displayed.
- Click the Proxy tab.
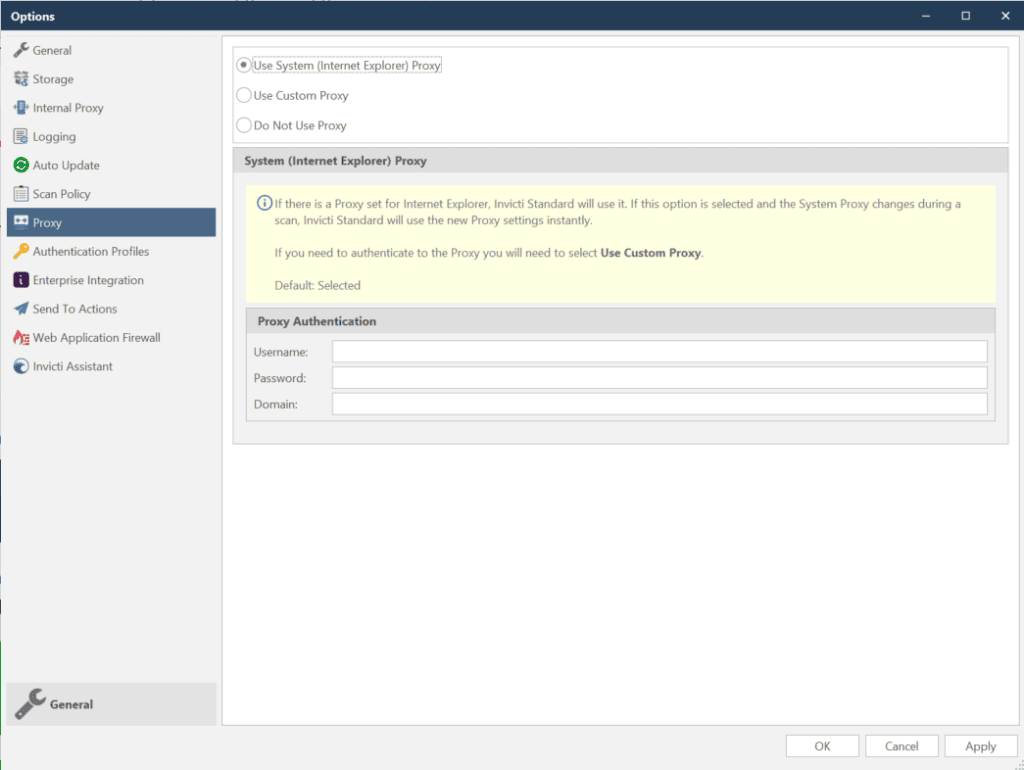
- Select the relevant Proxy option.
- Click Save.
Scanning a Website with Invicti Standard Using a SOCKS Proxy
By default, the Invicti Standard web vulnerability scanner does not support a SOCKS proxy. However, you can run the web security scan through a third-party proxy which then reroutes the traffic to your SOCKS proxy.
This procedure explains how you can use the free proxy server Privoxy to scan a website with Invicti Standard using a SOCKS proxy.
How to Install the Privoxy Proxy Server
- Privoxy is a free proxy server that is licensed under the GNU GPLv2. Download it from http://www.privoxy.org.
- Install it. And when you have set it up and it is running, open the main configuration file.
How to Configure Privoxy to Redirect to the SOCKS Proxy
To redirect the Privoxy traffic to the SOCKS proxy use the forward directives for the version of SOCKS proxy you are running, in order to specify the place to which the traffic should be redirected.
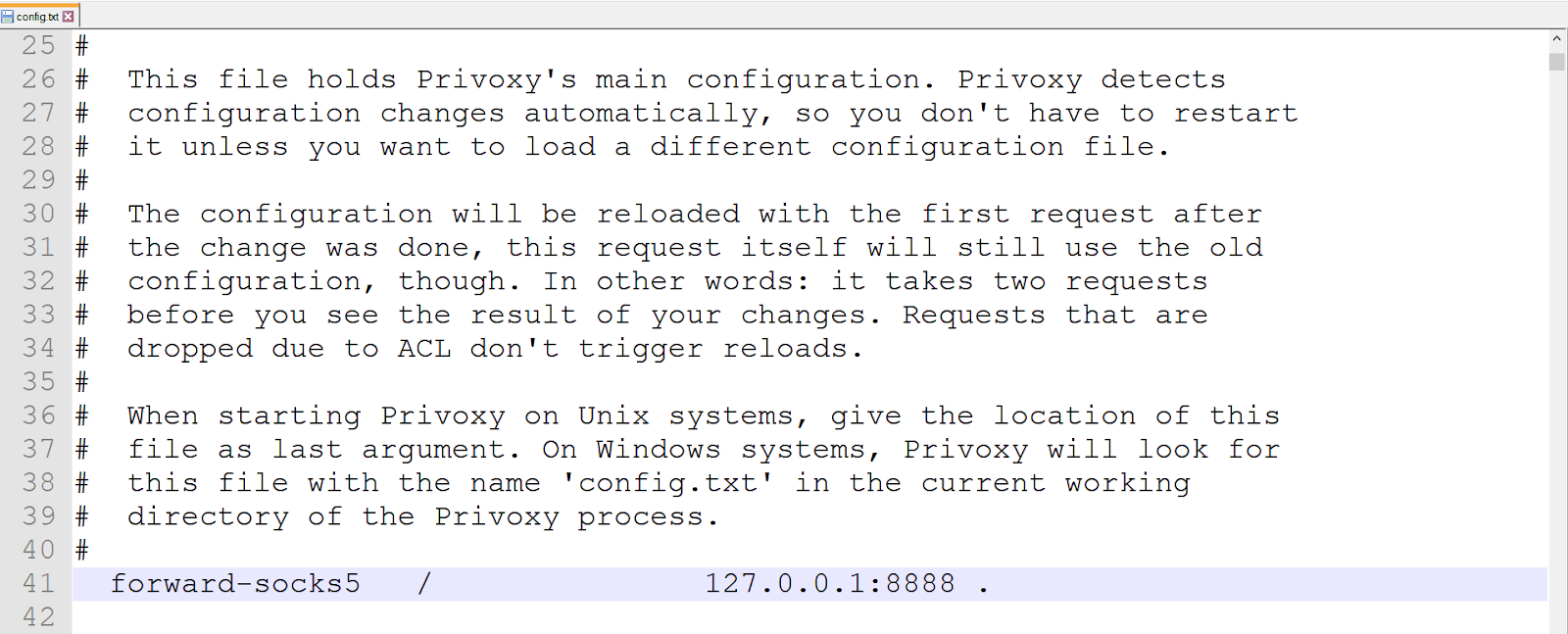
Since the SOCKS proxy listens on port 8888 and its address is 127.0.0.1, we’ll add the following directive in the Privoxy configuration:
forward-socks5 / 127.0.0.1:8888 .
This is a screenshot of the configuration we are running in our test environment.
For more information on the SOCKS proxy directives and forwarding traffic with Privoxy, see the Forwarding section in the Privoxy 3.0.28 User Manual.
Configuring Invicti to Use Privoxy Proxy
By default, the Privoxy proxy server listens on port 8118 on localhost.
For further information on Scan Policies and the Scan Policy Editor, see Scan Policy Editor.
How to configure Invicti to Redirect the Traffic Through the Privoxy Proxy Server Running on the Same Machine
- Open Invicti Standard.
- From the Home tab, click the Scan Policy Editor. The Scan Policy Editor dialog is displayed.
- Select the Scan Policy you’d like to use.
- From the HTTP section, click the Proxy tab.
- Select the Use Custom Proxy option.
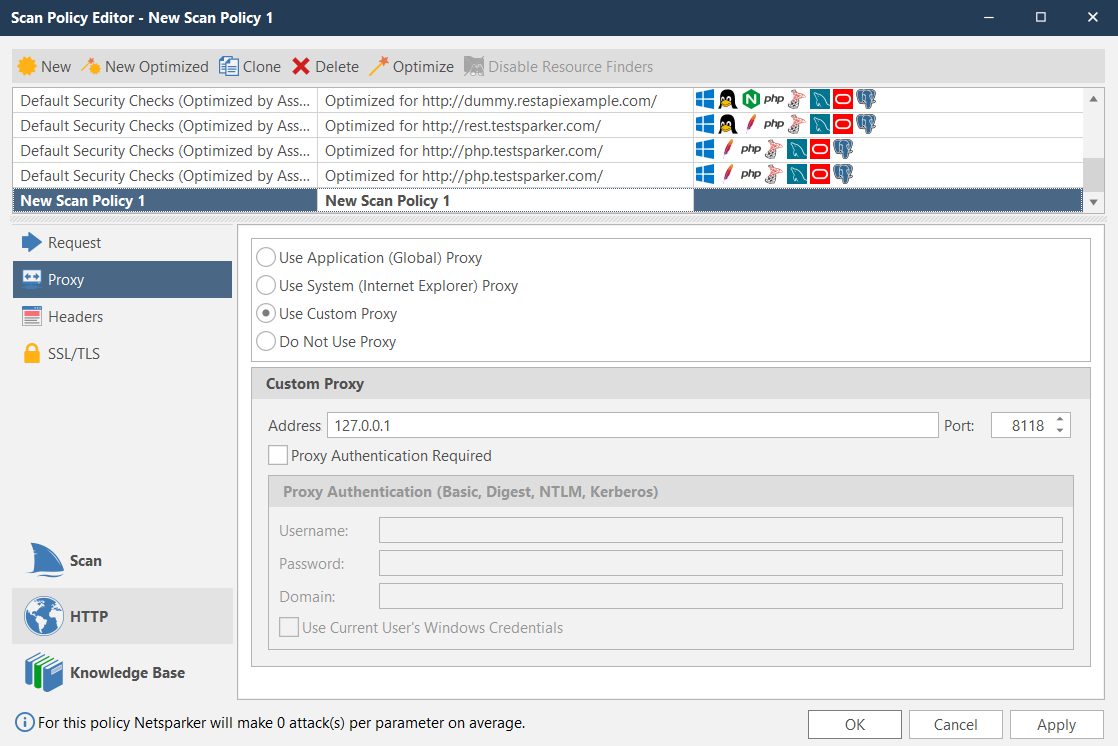
- Enter the Address and Port.
- Click OK. Invicti Standard will forward all the traffic by the Privoxy server, which will route the traffic through the SOCKS proxy. This is displayed in Invicti Standard’s status bar.
