What is Invicti?
Invicti is an automated, yet fully configurable, web application security scanner that enables you to scan websites, web applications, and web services, and identify security flaws. Invicti can scan all types of web applications, regardless of the platform or the language with which they are built.
- Invicti is the only online web application security scanner that automatically exploits identified vulnerabilities in a read-only and safe way, in order to confirm identified issues.
- It also presents proof of the vulnerability so that you do not need to waste time manually verifying it. For example, in the case of a detected SQL injection vulnerability, it will show the database name as proof of exploit.
Our scanning technology is designed to help you secure web applications easily without any fuss, so you can focus on fixing the reported vulnerabilities. If Invicti cannot automatically confirm a vulnerability, it will inform you about it by prefixing it with ‘[Possible]’, and assigning a Certainty value, so you know what should be fixed immediately.
Key Concepts
This is a list of key concepts in Invicti.
| Concept | Description |
| Highly accurate | Invicti produces highly accurate web application security scans, whose vulnerabilities are verified, proving that they are not false positives. |
| Proof-Based ScanningTM | Our Proof-Based Scanning technology actively and automatically verifies detected vulnerabilities, confirming that they are real and not false positives, by exploiting them in a read-only and safe manner. Depending on the type of vulnerability, Invicti will generate proof. Some vulnerabilities also allow you to exploit them manually or generate a Proof of Concept. For further information, watch The Proof-Based Web Vulnerability Scanning Technology. It’s completely safe. For example, when exploiting a SQL injection vulnerability and generating a proof of exploit for it, the scanners will only try to read data from the database, not write or delete data from the database. |
| Proof of Concept | Invicti identifies vulnerabilities, then it safely exploits them during the web vulnerability scan. This Proof of Concept is the actual exploit that proves that the vulnerability exists. And, it’s useful if you need to reproduce the vulnerability for a developer. This is what an XSS vulnerability report looks like, where the Proof URL is what Invicti uses to exploit the vulnerability. |
| Proof of Exploit | A proof of exploit is used to report the data that can be extracted from the vulnerable target once the vulnerability is exploited, demonstrating the impact an exploited vulnerability can have and proving that it is not a false positive. This is what it looks like in the case of an SQL Injection vulnerability, as reported in Invicti Enterprise. Invicti scanners can generate proof when they identify the following vulnerability types: SQL Injection Boolean SQL Injection Blind SQL Injection Remote File Inclusion (RFI) Command Injection Blind Command Injection XML External Entity (XXE) Injection Remote Code Evaluation Local File Inclusion (LFI) Server-side Template Injection Remote Code Execution Injection via Local File Inclusion If Invicti is unable to automatically prove the vulnerability exists, you will be advised so that you can double-check its findings.  |
| Vulnerabilities | A vulnerability is a security weakness in your website or web application that provides an opening for malicious hackers to gain access, get access to data or exploit for illegitimate or illegal purposes. |
| Issues | An Issue is the name, type, date, and other details of any detected vulnerability. (see Issues). |
| Severities | Each vulnerability is assigned a different severity or threat level according to the damage it could do and the urgency with which it requires fixing (see Vulnerability Severity Levels). |
| Scan Policies | Invicti allows you to use Scan Policies in order to determine and specify the type, range, and targets of your scan according to your needs. (see Scan Policies). |
| Scheduled Scans | Scans can be launched immediately or they can be scheduled for times when it best suits you, including at regular intervals. (see Scheduling Scans). |
| Integrations | Invicti integrates with a wide range of software and tools that enable you to connect with your existing SDLC, including vulnerability management systems, issue tracking systems, continuous integration systems, single sign-on providers, team messaging systems, and web application firewalls. (see Integrations). |
Benefits of Proof-based Scanning Technology
These are some of the key benefits of automating the post-scan process:
- You do not have to manually verify detected vulnerabilities the scanners found, saving time that you can use to fix them
- You do not have to be seasoned security professional to use the Invicti security scanners, since results are automatically confirmed for you (and there is no need to know how to reproduce the findings)
- The process of finding vulnerabilities in web applications will cost you less since you can assign it to less technical people.
- If you are a QA, you won’t be sent back by the developers to prove that there is a vulnerability in their code
- As a developer or service provider, you do not need to convince your superior or customer to fix their issues, simply show them the proof!
The accuracy of Invicti’s Proof-Based Scanning currently stands at slightly over 99.98%, according to the company’s security researchers that reviewed the last 5 years’ statics.
This accuracy means that when Invicti marks a vulnerability as confirmed, you can be 99.98% sure that the issue is real, exploitable, and not a false positive.
Also, the research revealed that Invicti provides accurate automatic confirmation for 94.74% of all direct-impact vulnerabilities it detects. For further information, see Proof-Based Scanning: No noise, just facts.
What is the Difference Between Invicti Enterprise and Invicti Standard?
Invicti Enterprise is a scalable, multi-user web application security solution and Invicti Standard is an on-premises desktop web vulnerability scanner.
Invicti Crawling and Scanning Technology
Invicti has industry-leading scanning technology. Both editions are built around the same crawling and Proof-based Scanning technology. Therefore, in terms of web application coverage, detection of vulnerabilities, and security flaws, you get the same results.
Overview of Both Invicti Web Application Security Scanners
The Standard edition of Invicti was built for those who are more hands-on – security engineers, penetration testers, and developers – and scan typically less than 50 websites.

Invicti Enterprise is a scalable, multi-user online vulnerability scanner with built-in enterprise workflow and testing tools. Because it is a browser-based cloud platform, you do not need to buy, license, install or support hardware or software. You can also launch as many web application security scans as you want within minutes.
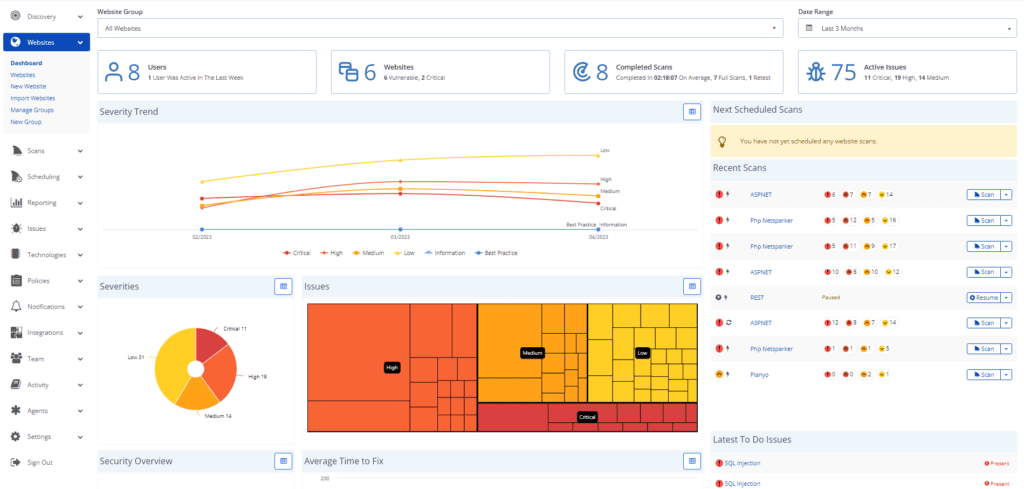
Scalability of Service
Scalability is the major difference between the editions. The resources of Invicti Standard are limited to the specifications of the hardware on which it runs. It was designed to scan one or several applications at a time. If you need to scan multiple websites at the same time, you can manually launch multiple instances of the Standard scanner. The advantage of Invicti Enterprise is that, since it is a hosted web vulnerability scanner, its resources are virtually unlimited, thanks to Amazon’s Cloud (AWS) infrastructure.
Feature Highlight: Website Groups
Invicti Enterprise enables you to group websites, configure generic scan settings and launch or schedule a web security scan with a single click.
Keeping Up with the Latest Web Security Threats
Follow our web application security blog and you will notice that we frequently release software updates. In fact, our list of vulnerabilities checks grows daily. Releasing frequent updates ensures that you can scan your web applications against the latest security threats and vulnerabilities. The response time for releasing new security checks is also critical especially when a vulnerability such as Apache Struts is discovered and being exploited in the wild.
- Invicti Standard checks for updates every time it is launched. You can apply updates in minutes.
- Invicti Enterprise is maintenance-free. We update the service and updates are automatically available.
Web Security Scanner Adaptability
Typically, desktop software is more configurable than an online service. The reason is that an online service is built around an engine that is designed to cater to a wider variety of customers. Therefore, it has fewer configurable parameters, resulting in a number of limitations.
But, this is not the case with Invicti. Anything that can be configured in Invicti Standard can also be configured in Invicti Enterprise, such as the URL rewrite rules and other crawling options, HTTP connection properties, and other scan policy settings.
Team Collaboration
- Invicti Standard is a desktop application that is designed for a single user who has access to the computer on which it is installed.
- Invicti Enterprise is a multi-user environment. Every team member has their own user account in the Invicti Enterprise edition and can launch web application security scans and view reports and issues with the proper privileges. As an administrator, you can configure different privileges for each user.
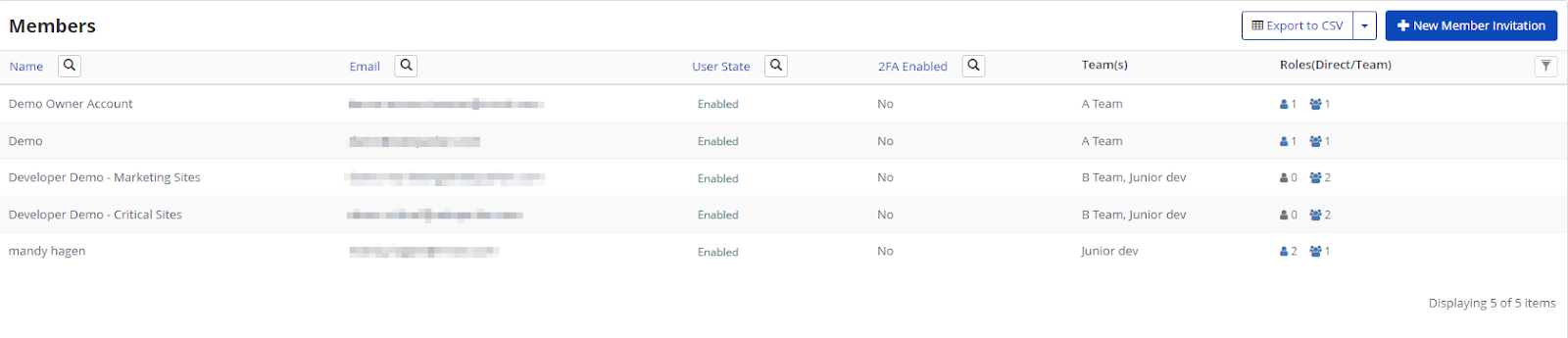
Feature Highlight: Vulnerability Management and Tasks
Just like dedicated bug tracking systems, Invicti Enterprise enables you to assign identified vulnerabilities as tasks to team members for remediation. This is an essential feature when you are tracking the security of many web applications.

Tasks marked as Fixed (Unconfirmed) are automatically rescanned. Depending on the result, they are either closed or reopened and reassigned.
The vulnerability management system is designed to ensure every user knows what they need to do, and for results and fixes to be checked automatically. You can also integrate your existing bug tracking solution.
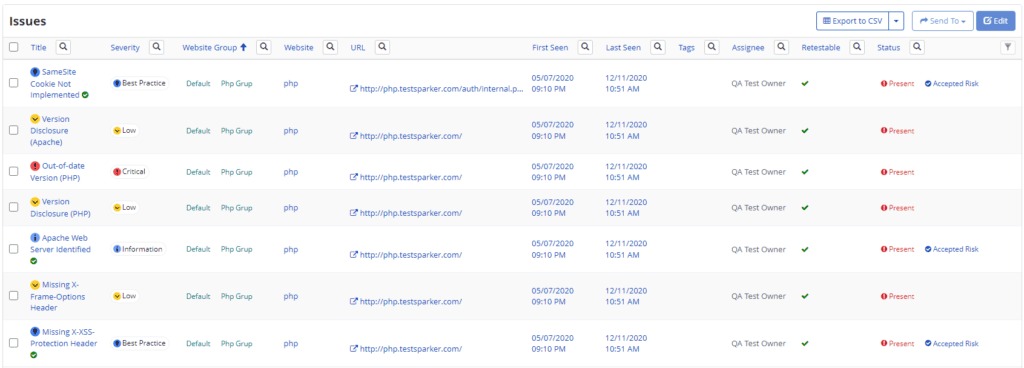
Web Application Security Scans in Your SDLC
Both Standard and Enterprise editions can be easily integrated into your SDLC and Continuous Integration processes.
- Invicti Standard has command-line support allowing you to easily write scripts that can be triggered by other applications to launch automated scans.
- Invicti Enterprise has an extensive and well-documented API that you can use to trigger any type of action available in the Invicti Enterprise dashboard.
Keeping Web Applications Secure
Launching a single web application security scan and remediating the identified vulnerabilities can be quite difficult. It is even more demanding to scan all web applications frequently and ensure that detected vulnerabilities are fixed and that the applied fixes do not open new security flaws.
- If you use Invicti Standard, you can compare different scan results on the same website. Our Retest and Incremental scans allow you to pinpoint the differences between scans and keep track of all issues. It’s easy to compare results, but time-consuming if you have lots of websites.
- This is where Invicti Enterprise shines. Its trending and correlated reports are automatically updated each time a website or web application is scanned. This negates the need to compare results manually.
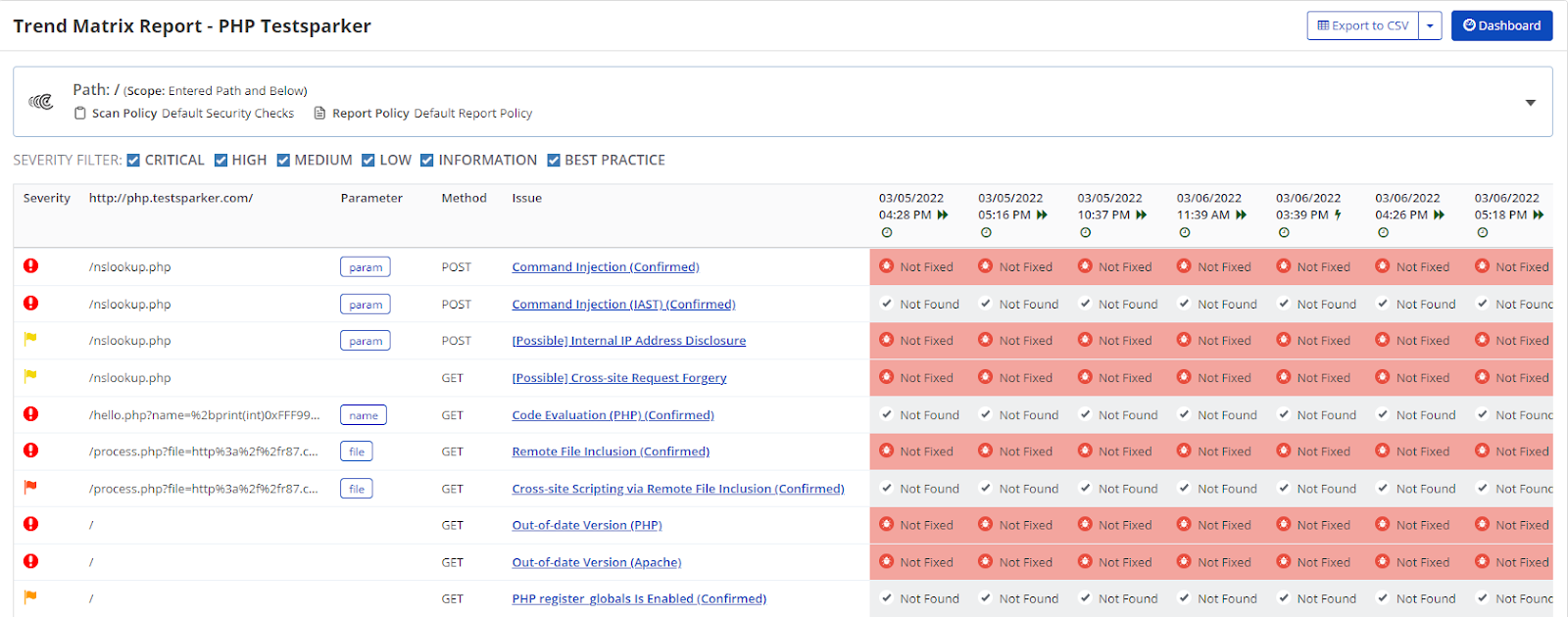
Manual Crawling and Security Scanning
If you need to manually crawl a website or a section of it, you’ll need to proxy the traffic through the scanner so it will capture it, identify attack surfaces and then scan them. Invicti Standard can be used for manual crawling.
With Invicti Enterprise, you cannot, as it is a cloud-based product. Nevertheless, you can still achieve the same results by configuring a browser to proxy the traffic through a local proxy (such as Fiddler) and capture the traffic. Once you capture the traffic, you can import the Fiddler capture to Invicti Enterprise and launch the scan.
Enterprise or Standard Web Application Security Scanner?
- If you have a small team and a small number of websites, and you prefer to be more hands-on, Invicti Standard is the best option.
- If you operate in a large team and have many websites and web applications to secure, and need supporting tools to ensure collaboration among the team members, Invicti Enterprise is recommended. You will also have access to the Invicti Standard edition for each user.

